Cloud identities-Describe security, compliance, privacy, and trust in Microsoft 365
Because AD DS can perform its functions only when both the user and the resources to be accessed are located on-premises, it is not a viable solution for cloud-based applications and services. Therefore, Microsoft had to devise an alternative authentication and authorization solution for its cloud-based products, such as Microsoft 365. This solution is Entra ID, a cloud-based directory service alternative (or companion) to AD DS in which administrators create cloud identities. Azure AD is currently undergoing a name change. All Microsoft identity management tools are being added to the new Microsoft Entra product family. Azure Active Directory will soon be known as Microsoft Entra ID.
Microsoft 365 relies on the Entra ID service for its identity management, and all Microsoft 365 services use Entra ID for authentication and authorization. Microsoft 365 subscribers (as well as Office 365 and Windows Azure subscribers) become Entra ID tenants automatically. When a user accesses a Microsoft 365 application in the cloud, as shown in Figure 3-6, Entra ID is the invisible intermediary that confirms the user’s identity with the authentication mechanisms the Microsoft 365 administrators have selected. In the same way, Entra ID authorizes the user’s access to the application and to the files the user opens in the application.
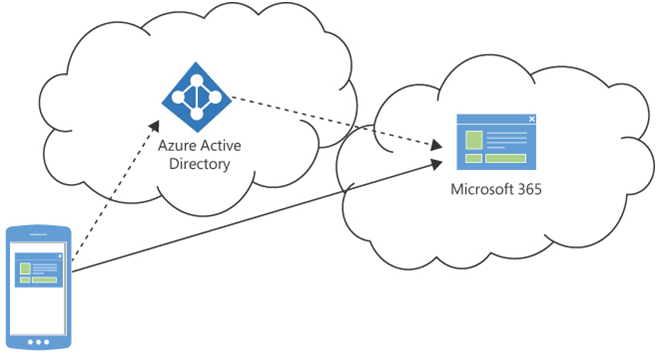
FIGURE 3-6 Azure Active Directory provides authentication and authorization services for Microsoft 365 applications and services
Unlike AD DS, administrators don’t need to install multiple domain controllers for Entra ID or configure directory replication. An Entra ID tenancy is automatically replicated to multiple datacenters in the Microsoft Global Network. Also, unlike AD DS, Entra ID uses a single master replication model. There is only one primary replica of an Entra ID tenant, and all new users and account modifications are written to that primary replica. The changes are then automatically replicated to multiple secondary replicas at different datacenters, as shown in Figure 3-7. The secondary replicas handle all incoming read requests using the replica closest to the requesting user, application, or service. Because there are many secondary replicas, the Entra ID service is always available. Because there is only one primary replica, it works differently by using a deterministic failover procedure.
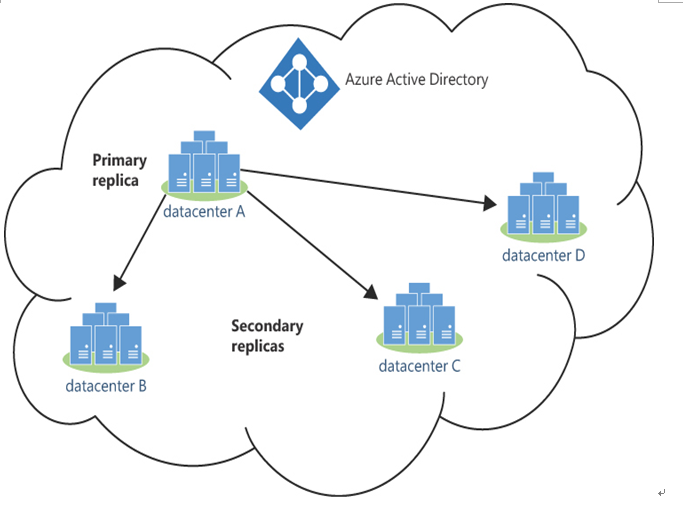
FIGURE 3-7 Azure Active Directory single master replicationAdministrators can use several tools to create users in Entra ID, including the Microsoft 365 admin center and the Azure Active Directory admin center. Azure ID’s authentication and authorization are also token-based, but the protocols and procedures used by Entra ID differ from those used by AD DS. Instead of Kerberos, Entra ID uses OAuth 2.0 or OpenID Connect.
