Describe cloud identity, on-premises identity, and hybrid identity concepts-Describe security, compliance, privacy, and trust in Microsoft 365
Every computer or mobile device can maintain a user’s identity and employ it to protect the device from being accessed by anyone else. However, when the user wants to access applications, services, or data from the company network, they need another identity; this identity is created and maintained by the network’s administrators and stored on the network, not on the user’s computer or another device.
On-premises identities
Beginning with the Windows 2000 Server release, enterprise identities were stored in Active Directory, an on-premises directory service still a part of the Windows 2019 Server product, although it is now called Active Directory Domain Services (AD DS). Installing the AD DS role on a Windows Server computer enables it to function as a domain controller, which contains an object-oriented database of user identities and other network resources, including groups, computers, and applications. AD DS is a domain-based hierarchical database that uses container and organizational unit objects to separate users and other resources into logical collections, which usually represent the departmental or geographic divisions of the company.
Typically, enterprise networks have multiple domain controllers, which administrators configure to synchronize the contents of their AD DS databases with each other for fault tolerance and high availability purposes. AD DS uses multiple master replication, meaning administrators can create or modify users and other objects on any domain controller, and the changes will be replicated to all of the other domain controllers, as shown in Figure 3-4.
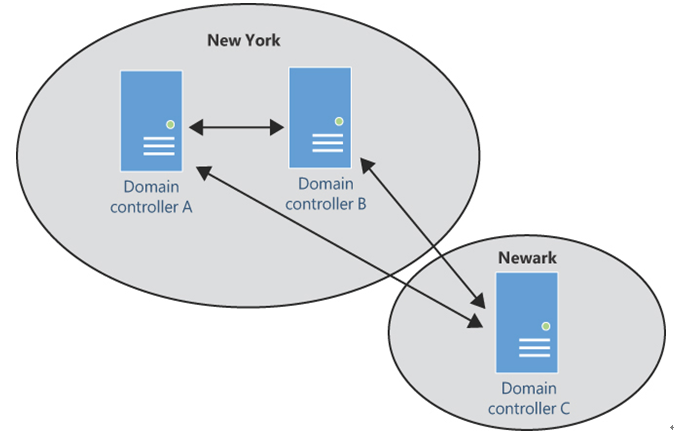
FIGURE 3-4 Active Directory Domain Services multiple master replication
Administrators can create AD DS user objects using graphical tools, such as Active Directory Users and Computers, as shown in Figure 3-5, or command-line tools, such as the New-ADUser cmdlet in Windows PowerShell.
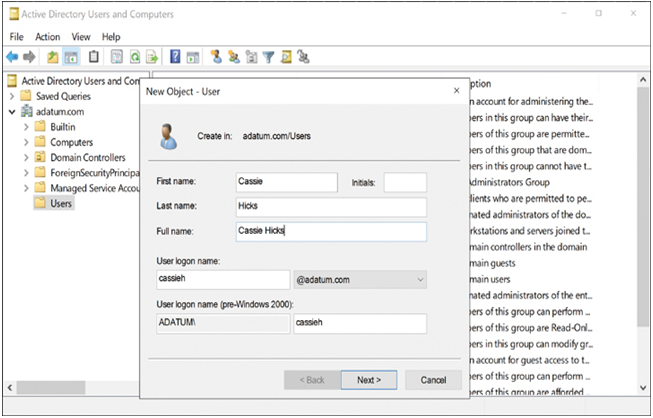
FIGURE 3-5 The New Object – User dialog box in the Active Directory Users And Computers console
The user objects in AD DS are strictly on-premises identities. Domain controllers must be located within the network perimeter and not directly accessible from the Internet. When users access on-premises resources, their identities are authenticated and authorized by the nearest domain controller, which uses a protocol called Kerberos to perform a complicated ticket-based authentication procedure. Users outside the network perimeter can only perform an AD DS sign-in to the network by establishing a VPN connection to a remote access server. This gives users a presence on the internal network, enabling them to access internal resources.
