Describe the identity and access management capabilities of Microsoft Entra ID-Describe security, compliance, privacy, and trust in Microsoft 365
An identity is a logical representation of a user in a network environment. To users, an identity is a name they type to sign in to the network, along with a password or other means of authentication.
To administrators, an identity is a collection of attributes associated with a particular individual, as shown in Figure 3-1. The sign-in name is one of those attributes, but there can be many others, including personal information, such as a home address, telephone number, job title, and so on.
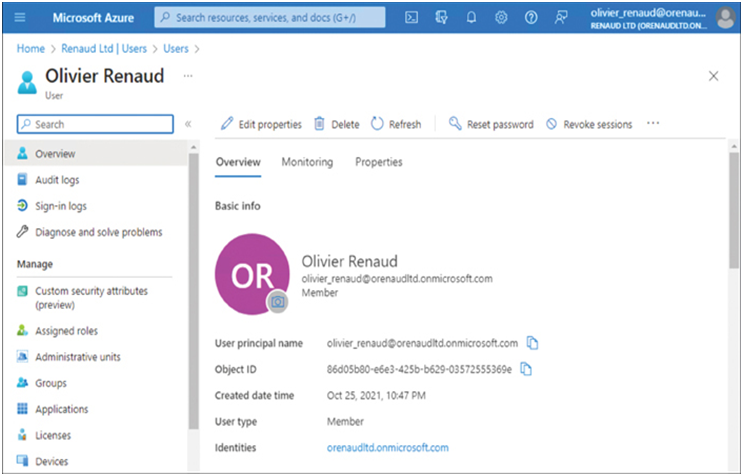
FIGURE 3-1 User attributes in Microsoft Azure Active Directory
An identity also typically includes a list of the groups to which the individual is a member. Administrators use groups to assign rights and permissions to individuals. When a group is assigned rights and permissions to access network resources, all the group’s members automatically inherit those rights and permissions. This is an efficient alternative to assigning multiple rights and permissions to each user identity individually.
Microsoft 365 and Directory Services
A directory service is a service or software product that stores information about network resources to unify them into a single, manageable entity. For example, the Domain Name System (DNS) is a directory service that associates the names of network resources with their corresponding IP addresses.
Entra ID and Active Directory Domain Services (AD DS) are the directory services that store and manage user identities for the various Microsoft 365 components. Entra ID stores its directory information in the Microsoft Azure cloud, and AD DS is stored on Windows servers configured to operate as domain controllers.
Note Azure AD Name Change
As of this writing, Microsoft is currently in the process of changing the product name of Azure Active Directory to Microsoft Entra ID. Microsoft Entra is a new product family that includes all of Microsoft’s identity management tools. The MS-900 objectives mention that Azure AD is part of Microsoft Entra, but the name Entra ID will eventually replace Azure AD entirely.
Entra ID is available in three plans, as shown in Table 3-1. All Microsoft 365 products include either the Premium P1 or Premium P2 plan.
TABLE 3-1 Azure Active Directory licenses
| Azure Active Directory License | Included with |
| Azure Active Directory Free | Office 365 or Microsoft Azure, Dynamics 365, Intune, and Power Platform subscriptions |
| Office 365 Apps | Office 365 E1, E3, E5, F1, and F3 |
| Azure Active Directory Premium P1(Microsoft Entra ID P1) | Microsoft 365 Enterprise E3 and Microsoft 365 Business Premium |
| Azure Active Directory Premium P2(Microsoft Entra ID P1) | Microsoft 365 Enterprise E5 |
The Azure Active Directory Premium P1 plan supports the following features and services:
- Unlimited directory objects Enables administrators to create cloud identities for unlimited users.
- User and group management Enables administrators to create and manage user and group identities using cloud-based tools, such as the Entra admin center and the Microsoft 365 admin center.
- Cloud authentication Enables users to sign on to the network using hybrid identities stored in the cloud and with password hash synchronization or pass-through authentication.
- Synchronization with AD DS using Azure AD Connect After installing the Azure AD Connect tool on an AD DS domain controller or on-premises server, on-premises identities can be replicated to the Entra ID directory in the cloud. This creates hybrid identities enabling users to access cloud-based and on-premises resources with a single sign-on.
- Seamless single sign-on Enables users with hybrid identities connected to the on-premises network to sign in with no interactive authentication procedure.
- Support for federated authentication Enables administrators to offload the Entra ID authentication process to a federated service, such as Active Directory Federation Services.
- Multifactor authentication using phone, SMS, or app Enables administrators to require that users supply two or more forms of identification when signing in with an Entra ID identity, such as a password plus a biometric scan or a one-time code sent to the user’s smartphone.
- Support for hybrid user access to cloud and on-premises resources Enables users with hybrid identities to access both cloud-based and on-premises resources after a single Entra ID authentication.
- Self-Service Password Reset Enables users with cloud-based identities to modify their passwords without administrator assistance.
- Device write-back from Entra ID to AD DS identities Enables devices registered in Entra ID and modified cloud identity passwords to be copied to an AD DS container. Ordinarily, Azure AD Connect synchronizes data only from AD DS to Entra ID.
- Application proxy Enables cloud-based remote users to access internal web applications by forwarding their requests to a connector running on an on-premises server.
- Dynamic groups Enables administrators to create rules specifying the attributes a user account must possess to be automatically added to a group.
- Group naming policies Enables administrators to create policies that specify a format for group names. For example, group names can be required to specify a function, a department, or a geographic location.
- Conditional access Enables administrators to specify conditions that mobile devices must meet before they are granted access to cloud-based resources, such as sign-in risk, client app in use, the state of the mobile device, and the device’s location.
- Microsoft Identity Manager Provides identity and access management, including synchronization of users, groups, and other objects for AD DS and Entra ID, as well as third-party directory services.
- Azure Information Protection Premium P1 Enables users and administrators to classify and label documents based on the sensitivity of the data they contain.
- Security and activity reporting Provides administrators with reports that list potential threats, including risky sign-ins and audit logs that document user activities.
With these features and services, the Azure Active Directory Premium P1 plan enables administrators to manage an organization’s cloud-based resources and identify, predict, detect, and remediate a wide variety of security threats. However, the Azure Active Directory Premium P2 plan supports everything included in the P1 plan and also provides the following additional security features:
- Microsoft Defender for Identity (Azure AD Identity Protection) Evaluates users’ sign-in activities, quantifies their risk levels, and takes action based on those levels.
- Privileged Identity Management Enables administrators to regulate access to sensitive resources by granting temporary privileges to specific users, requiring additional security measures, and receiving notifications when the resources are accessed. The objective is to prevent users with administrative privileges from using them unnecessarily.
- Microsoft Defender for Cloud Apps (Cloud App Security) A cloud-based service that analyzes traffic logs and proxy scripts to identify and monitor the apps that users are accessing.
- Azure Information Protection Premium P2 Expands on the capabilities of the Premium P1 plan by automating the process of identifying, classifying, and labeling documents.
