Enterprise Mobility + Security-Describe Microsoft 365 apps and services
The Microsoft 365 components concerned with managing mobile devices and their protection are collectively known as Enterprise Mobility + Security (EMS). The primary tools that compose EMS and the functions they provide for mobile devices are as follows:
- Azure Active Directory Contains the accounts that provide users with single-sign-on capability for all the Microsoft 365 applications and services. Administrators can configure user accounts to require multifactor authentication to enhance the security of mobile devices.
- Microsoft Intune Enrolls mobile devices and associates them with particular users or groups. Using Intune, administrators can specify whether to use Mobile Device Management (MDM) or Mobile Application Management (MAM), specify device compliance policies, and create device configuration policies.
- Azure Information Protection Provides document-level security by applying labels that classify the information files΄ sensitivity and applying protection to specific documents through encryption, user restrictions, and other means.
- Microsoft Advanced Threat Analytics Gathers information from many Microsoft 365 enterprise sources and analyzes it to anticipate, detect, and react to attacks and other security threats.
The following sections examine some of these components in greater detail.
Microsoft Endpoint Manager
Microsoft Endpoint Manager is a cloud-based portal that works with Microsoft Intune to provide detailed information and administrative access for enrolled devices, such as their hardware properties, serial numbers, installed apps, and other configuration data. However, as of October 2022, the Microsoft Endpoint Manager name has been deprecated, and the product’s functionality has been incorporated into the Microsoft Intune admin center. Although the list of admin centers in the Microsoft 365 admin center portal still includes an Endpoint Manager link, clicking it opens the Microsoft Intune admin center.
Microsoft Intune
Microsoft Intune is the tool administrators use to enable the enrollment of users’ personal devices into Microsoft 365 and regulate their capabilities. Mobile Device Management (MDM) enables administrators to take near-complete control of enrolled devices, even to the point of issuing remote commands that erase all company data on the device.
Exam Tip
Microsoft has announced that its collection of endpoint management tools will now be known as the Microsoft Intune family of products. Therefore, the name Microsoft Intune can refer to the individual application or the family of products, including Windows Autopilot, Configuration Manager, and Desktop Analytics. Candidates for the MS-900 exam should be cautioned against confusing the individual product with the product family.
For users who do not like the idea of the organization exercising that kind of control over their personal property, Mobile Application Management (MAM) provides devices only with managed applications, leaving the rest of the device unrestricted. Which option administrators choose must depend on the sensitivity of the data that might be stored on the device and any security compliance guidelines the organization must observe.
Note MDM and MAM
For more information on Mobile Device Management and Mobile Application Management, see the “Mobile Device Management” section later in this chapter.
Administrators configure Microsoft Intune settings using the Microsoft Intune admin center, as shown in Figure 2-48. All Intune settings are implemented and stored in the cloud.
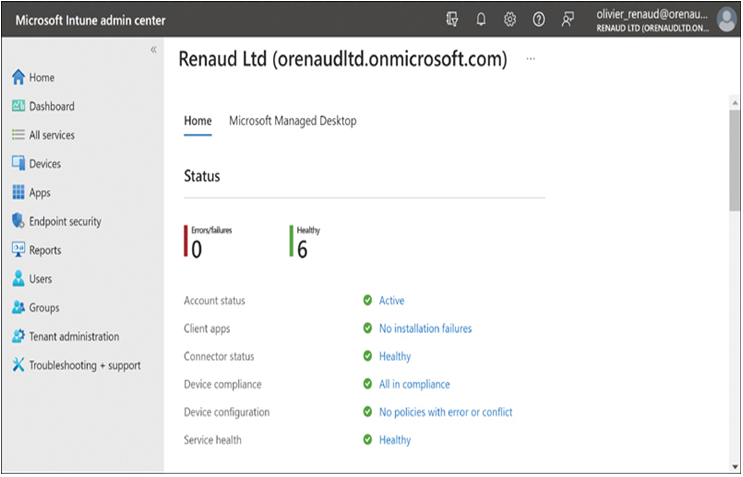
FIGURE 2-48 The Home page of the Microsoft Intune admin center
Microsoft Intune provides settings for a variety of endpoint security features, as shown in Figure 2-49. Administrators can configure these settings to ensure that users’ enrolled devices—even their personal devices—provide a safe environment for company data.
One of the most common methods for ensuring client devices are properly secured is assigning device compliance policies to them. Device compliance policies are rules that specify how a device must be configured for it to access Microsoft 365 services.
For example, a policy can require that mobile devices must have a password to unlock it, rather than a simple swipe (as shown in Figure 2-50), that data be stored on the device in encrypted form, and that the operating system on the mobile device updated to a specific level. A device that does not meet the compliance policy settings cannot be enrolled, and even when it is successfully enrolled, it must be checked for compliance at regular intervals to maintain its access to the Microsoft 365 cloud services.
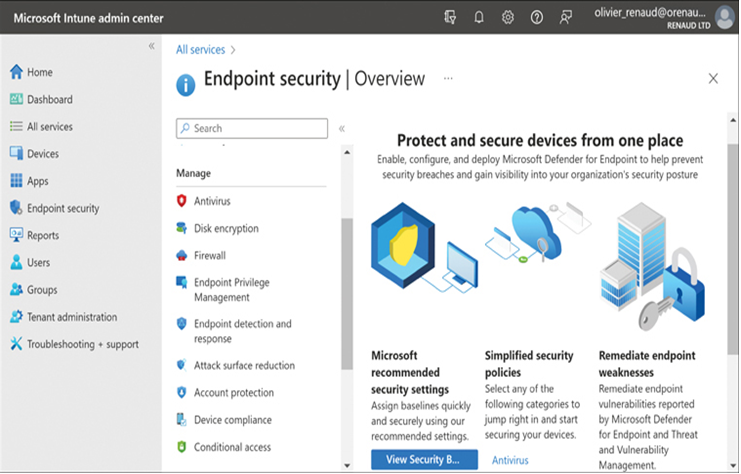
FIGURE 2-49 The Endpoint Security Overview page of the Microsoft Intune admin center
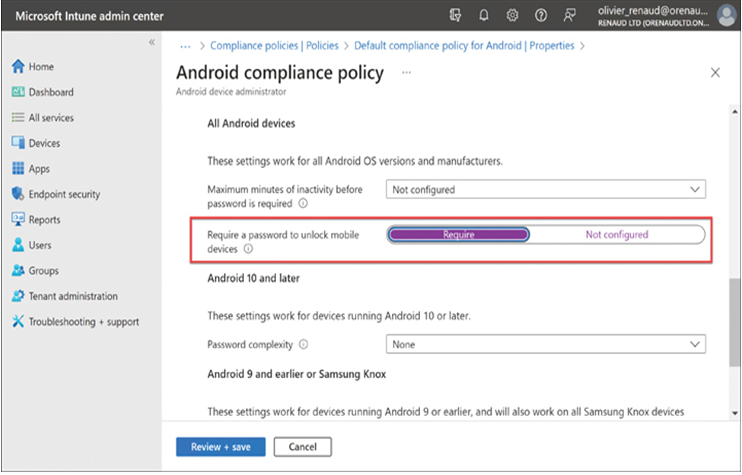
FIGURE 2-50 Device compliance policies in Microsoft Intune
Typically, protecting enterprise data on mobile devices restricts what the device user can do. In some cases, administrators might want to prevent the users from endangering sensitive data. Another major security issue is the possibility of data theft or destruction when a mobile device is lost or stolen. Administrators can control mobile device capabilities by creating configuration profiles in Microsoft Intune for the various platforms and enabling or disabling device functions, as shown in Figure 2-51.
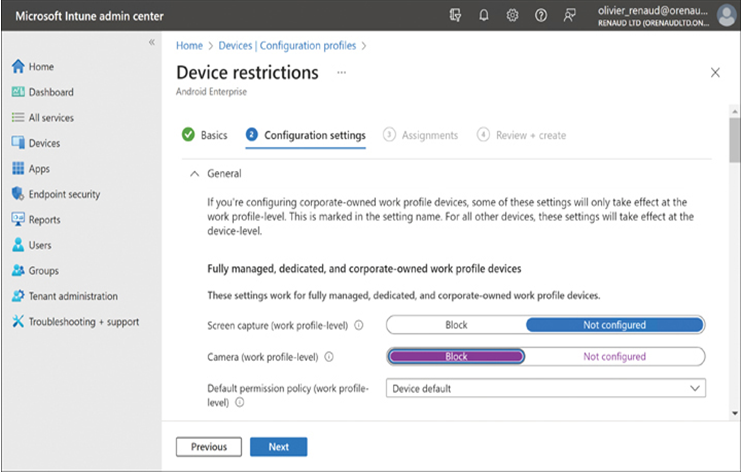
FIGURE 2-51 Device configuration profiles in Microsoft Intune
Administrators can further specify which applications mobile devices are permitted to run and also explicitly block them from running certain applications. Clearly, mobility is not just allowing devices to connect to a Microsoft 365 domain; their capabilities must also be restricted.
