Hybrid Identity Authentication-Describe security, compliance, privacy, and trust in Microsoft 365
While installing Azure AD Connect, an administrator must select the authentication method that Entra ID will use to provide users access to cloud resources. There are three options to choose from:
- Azure AD Password Hash Synchronization The simplest Azure AD Connect authentication method requires no additional infrastructure to implement. Azure AD Connect creates a hash of each user’s AD DS password hash and applies it to the corresponding Azure ID identity, allowing users to access both on-premises and cloud resources using the same password, as shown in Figure 3-9. Azure AD Connect updates the cloud identity passwords every two minutes without interrupting a session in progress when a password change occurs. Because the password hash synchronization model is fully implemented in the cloud, it shares the high availability of the other Microsoft cloud services. To ensure continuous operation, Microsoft recommends the installation of Azure AD Connect on two or more servers as a standby, preferably at different locations.
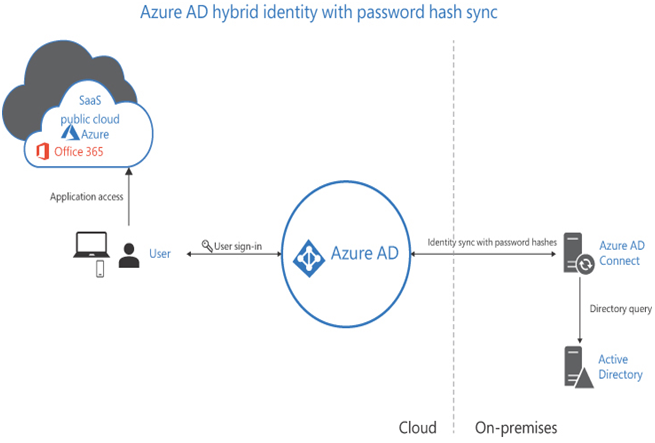
FIGURE 3-9 Entra ID password hash synchronization
- Entra ID Pass-Through Authentication Avoids all cloud-based password validation by using a lightweight pass-through authentication agent installed on on-premises servers. (Microsoft recommends three.) When users sign in to Entra ID, their requests are forwarded to the agent, which forwards them (in encrypted form) to a domain controller to validate the users against their on-premises identities in AD DS, as shown in Figure 3-10. The agents require only outbound Internet access and an AD DS domain controller, so they cannot be located on a perimeter network. The end result is the same user experience as password hash synchronization. Still, this method avoids storing user passwords in the cloud in any form and enables administrators to enforce on-premises Active Directory security policies, such as disabled or expired accounts. It allows sign-in hours and complies with contracted security requirements. It is also possible to deploy password hash synchronization and pass-through authentication to function as a backup in the event of an on-premises failure that prevents the agents from functioning.
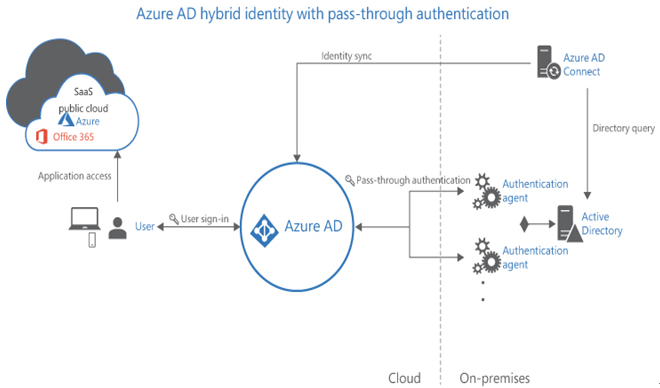
FIGURE 3-10 Entra ID pass-through authentication
- Federated Authentication Offloads the authentication process to an external solution that the organization trusts, such as Microsoft Active Directory Federation Services (AD FS). The configuration and management of the authentication process—as well as the user experience—are the responsibility of the federated system; Entra ID is not involved. Depending on the organization’s security requirements, the sign-in process with the federated system might be simpler or more complicated than that of Entra ID. The federated system typically consists of a load-balanced cluster of servers—called a farm—for high availability and fault-tolerance purposes. Because the federation servers require access to Entra ID and AD DS domain controllers, the servers (or proxy intermediaries) must be located in a screened subnet of an on-premises perimeter network, as shown in Figure 3-11. Organizations typically opt for the federated authentication option because they want to (or are compelled to) use an authentication method that Entra ID does not support, such as certificates or smart cards. The additional hardware, software, and administrative infrastructure the federated authentication method requires can be a significant extra expense. Organizations that choose this option often do so because they have already invested in the infrastructure. It is also possible to deploy password hash synchronization in addition to federated authentication to function as a backup in the event of an on-premises failure that prevents federation servers or their proxies from functioning.
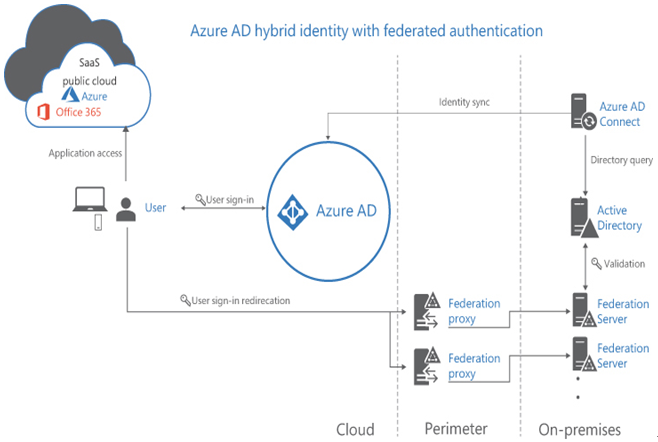
FIGURE 3-11 Federated authentication
Important Selecting an Authentication Method
Selecting a cloud authentication method for hybrid identities is a critical decision for administrators because it provides users with access to all the cloud resources and is the basis for many other security features in Entra ID. It is also important to note that changing the authentication method after the deployment is complete is difficult, so administrators should consider their options carefully.
